NOTE: Forcing QIE to use a new TLS Session with each connection can effect performance of the connection speed because a new TLS handshake will be required with each message.
QIE has been enhanced to allow for a java option to prevent the re-use of the TLS Session. Starting with build #9954, QIE will check for a java option, if the option is set to true, then it will not cache TLS sessions, and force a new handshake on every message sent across the secure socket connection.
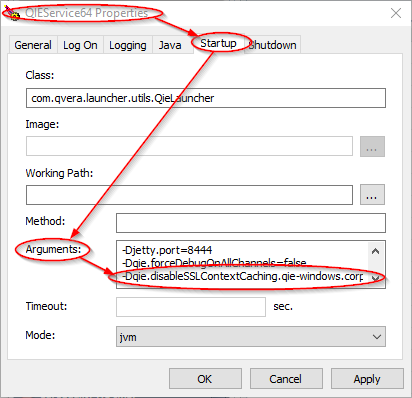
To set this option, first note the 'Host' and 'Port' from the destionation node.
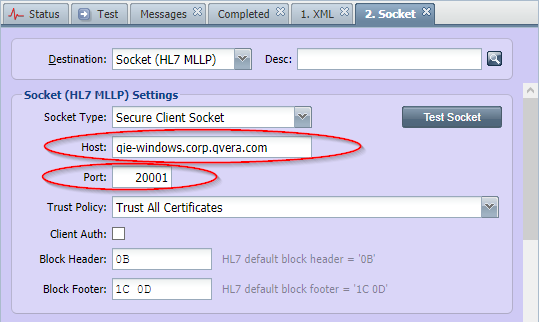
Then open the QIEService Properties dialog and go to the 'Startup' tab. From this tab, add the following java option to the 'Arguments' field.
-Dqie.disableSSLContextCaching.{host}.{port}=true
Replace the '{host}' with what is found in the destination host field, and replace the '{port}' with what is found in the destination port field. For example -Dqie.disableSSLContextCaching.qie-windows.corp.qvera.com.20001=true would be the java option for the above destination node.